System Security (Best Practices)
The application takes measures to safeguard your confidential data and protect the sensitive information that your customers share with you. But managers and business owners also play a large part in security practices by the policies that are enforced at the counter and throughout the premises.
Manage your system security and personally identifiable information (PII)
Restrict access permissions. The most efficient way to restrict access to various areas of the application is to make sure that each employee is assigned the appropriate role (Low, Medium, or High). This way, employees are restricted to the menus and functions that are necessary for them to complete their daily tasks.
Prohibit password sharing. To maintain accountability of each employee and make sure your operation is not vulnerable for access by terminated employees, do not allow employees to share user names or passwords.
Deactivate employees. Restrict access to unauthorized users by deactivating employees who have left your company, or who have been terminated. Deactivation removes employees from active lists while retaining a record of their past activity in the application for research and reporting purposes.
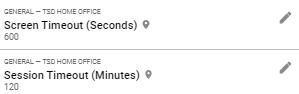
Use the Screen Timeout and Session Timeout settings. To protect on-screen information when an employee steps away from a screen, TSD DEALER offers a Screen Timeout management setting in Admin Setup to govern the number of seconds an employee must be idle (that is, without any mouse movement, clicking, or typing) before a privacy screen displays. Additionally, the Session Timeout setting governs the number of minutes an employee must be idle before the employee is automatically logged out.
Secure printed documents (and better yet, go digital). Make sure your operation is storing printed agreements and keys in a secure location out of the sight of customers. When it comes to customer information and signatures, consider using digital signature capture to save digital copies of signatures and uploading photos of insurance cards (including on the mobile app). This minimizes the need to store paper forms and photocopies that could be compromised.
Learn more
© 2026 TSD Rental, LLC
